Master the Fortinet NSE4_FGT-7.2 Exam with New and Authentic PDF Questions
Introduction: The Fortinet NSE4_FGT-7.2 exam is a crucial step for IT professionals aiming to validate their expertise in Fortinet Network Security technologies. In this article, we will explore the benefits of utilizing new and authentic Fortinet NSE4_FGT-7.2 exam PDF questions. These resources offer a reliable and effective way to prepare for the exam, equipping you with the knowledge and skills needed to succeed.
I. Understanding the NSE4_FGT-7.2 Exam: The NSE4_FGT-7.2 exam assesses your proficiency in deploying and managing Fortinet Network Security technologies. It covers a wide range of topics, including firewall policies, VPN technologies, intrusion prevention systems, security fabric architecture, and more. Understanding the exam structure and objectives is vital for efficient preparation.
II. Advantages of New and Authentic NSE4_FGT-7.2 Exam PDF Questions:
Comprehensive Coverage of Exam Topics: The new and authentic NSE4_FGT-7.2 Exam PDF questions provide comprehensive coverage of all the topics and subtopics included in the exam syllabus. These questions are meticulously crafted by industry experts and reflect the latest trends and updates in Fortinet Network Security technologies. By using these PDF questions, you can ensure that you have a solid understanding of the concepts required to excel in the exam.
Real Exam Scenario Simulation: The NSE4_FGT-7.2 Exam PDF questions are designed to simulate the real exam scenario, offering a realistic experience for candidates. The questions follow the format, structure, and difficulty level of the actual exam, allowing you to familiarize yourself with the exam environment and build confidence. Practicing with these PDF questions helps reduce exam-related anxiety and improves your chances of success.
Verified and Reliable Content: The new and authentic NSE4_FGT-7.2 Exam PDF questions undergo rigorous verification processes to ensure their accuracy and reliability. These questions are regularly updated to align with the latest exam syllabus and industry standards. By utilizing verified and reliable content, you can stay up to date with the evolving Fortinet Network Security technologies and make informed decisions during the exam.
Detailed Explanations and References: Each question in the NSE4_FGT-7.2 Exam PDF comes with detailed explanations and references to help you understand the underlying concepts and reasoning behind the correct answers. These explanations provide valuable insights and further consolidate your knowledge. By reviewing the explanations, you can address any knowledge gaps and enhance your overall understanding of Fortinet Network Security technologies.
III. Effective Strategies for Utilizing NSE4_FGT-7.2 Exam PDF Questions:
Develop a Study Plan: Create a study plan that incorporates dedicated time for practicing with the NSE4_FGT-7.2 Exam PDF questions. Allocate specific study sessions to review the questions, analyze the explanations, and reinforce your understanding of the exam topics.
Practice with Focus: Focus on specific exam topics or domains while practicing with the NSE4_FGT-7.2 Exam PDF questions. Identify areas where you feel less confident and allocate additional study time to strengthen your knowledge in those areas. This targeted practice allows you to make the most of your preparation and optimize your exam performance.
Time Management: Simulate the exam conditions by practicing with timed sessions using the Fortinet Exam PDF questions. Set a realistic time limit for each question or set of questions and strive to answer within the allocated time. This practice improves your time management skills, ensuring that you can effectively pace yourself during the actual exam.
Question 1
Which statement describes a characteristic of automation stitches?
AThey can have one or more triggers.
BThey can be run only on devices in the Security Fabric.
CThey can run multiple actions simultaneously.
DThey can be created on any device in the fabric.
Reveal Answer Next Question
Question 2
Which statement about video filtering on FortiGate is true?
AVideo filtering FortiGuard categories are based on web filter FortiGuard categories.
BIt does not require a separate FortiGuard license.
CFull SSL inspection is not required.
DOtis available only on a proxy-based firewall policy.
Reveal Answer Next Question
Question 3
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.

Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
AFortiGate allocates port blocks per user, based on the configured range of internal IP addresses.
BFortiGate allocates port blocks on a first-come, first-served basis.
CFortiGate generates a system event log for every port block allocation made per user.
DFortiGate allocates 128 port blocks per user.
Reveal Answer Next Question
Question 4
Refer to the exhibit.

Based on the ZTNA tag, the security posture of the remote endpoint has changed.
What will happen to endpoint active ZTNA sessions?
AThey will be re-evaluated to match the endpoint policy.
BThey will be re-evaluated to match the firewall policy.
CThey will be re-evaluated to match the ZTNA policy.
DThey will be re-evaluated to match the security policy.
Reveal Answer Next Question
Question 5
Refer to the exhibits.
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic. Exhibit B shows the HA configuration and the partial output of the get system ha status command.

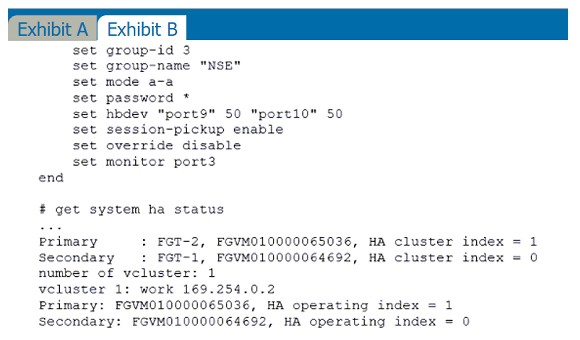
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
AFor non-load balanced connections, packets forwarded by the cluster to the server contain the virtual MAC address of port2 as source.
BThe traffic sourced from the client and destined to the server is sent to FGT-1.
CThe cluster can load balance ICMP connections to the secondary.
DFor load balanced connections, the primary encapsulates TCP SYN packets before forwarding them to the secondary.
Reveal Answer Next Question
Question 6
Which three statements are true regarding session-based authentication? (Choose three.)
AHTTP sessions are treated as a single user.
BIP sessions from the same source IP address are treated as a single user.
CIt can differentiate among multiple clients behind the same source IP address.
DIt requires more resources.
EIt is not recommended if multiple users are behind the source NAT
Reveal Answer Next Question
Question 7
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
AA CRL
BA person
CA subordinate CA
DA root CA